
Everything You Should Know About Secure Software Development Life Cycle Processes (SDLC)
Security is an integral part of a software development lifecycle process (SDLC).
For most organizations, creating and maintaining reliable software is primary, but securing is usually not considered elemental.
One of the main demanding parts of a software developer is ensuring their software’s development process creates secure software.
To avoid costly errors that leave software development cycles loosely developed and vulnerable, you need specific guidelines, clear directions, task lists, and structure.
This is where the secure software development life cycle comes in.
Secure SDLC offers more structure, erases miscommunication, and removes vulnerability risks.
This article lets you in on everything you need to know about secure software development life cycle processes.
We’ll cover:
- What is a secure SDLC?
- How does it work?
- Why is a secure SDLC important?
- What are the steps to a secure development lifecycle?
What is SDLC?
SDLC is the acronym for the framework Software Development Life Cycle, also referred to as secure development lifecycle. This framework helps developers and system engineers build applications and information systems by defining work phases and tasks.
They are used to not only plan information systems, but to build, test, and also deliver as well.
An SDLC should be able to give higher frequency and speed to the software deployment.
Several issues arise during software development from the decommissioning stage. But a software development life cycle framework helps identify these issues and their solutions along the way.
Developers have different software development life cycles. But the models are usually similar.
From the architecture and design to test planning, coding, testing, release and maintenance, development teams usually follow these phases for a solid software development life cycle process.
What is a Secure SDLC?
A secure SDLC refers to adding security details in the whole software development life cycle process. It follows a gradual approach to create scalable software to streamline the software or product pipeline.
Besides, secure SDLC also develops features that optimize the software’s maintenance, design, or deployment. And it’s an integral part of development in any modern software company.
Its long-term benefits cannot be overemphasized, seeing that it makes security the central part of each secure SDLC step and process.
The secure SDLC helps in the timely recognition of risks and vulnerabilities in the application/software security. While doing this, it makes sure that the matter of a secure SDLC is an uninterrupted process.
What’s more, those involved in the whole secure software development life cycle process become mindful and alert of security risks as they come up. Besides, secure SDLC also curtails excesses in handling threats.
Less time, effort, and cost are spent trying to relieve the risks that the secure SDLC helps detect. In all, with the secure SDLC process, you get applications or software that are free from a security compromise.
The whole secure development lifecycle process becomes one that prioritizes strategies for testing and fixing even before decommissioning.
Why Is A Secure Software Development Life Cycle Important?
A Secure SDLC process is vital in application security because it shows developers possible software threats during the development phase.
It is easier and cheaper to utilize secure SDLC than to put out products that are riddled with security loopholes and bugs. Having a secure SDLC is essential in ensuring that your software is free from potential hacking attacks.
In a world with as many genuine users as atrocious ones, anyone with ugly intentions could access source codes and wreak havoc. Software projects done without a secure development lifecycle are open to threats and security risks.
Developers may code with potential risks in mind and integrate newer security measures into the whole process as they go on.
The secure software development process isn’t finished until all phases have been carried out successfully. One of the most significant importance of the secure development life cycle process is control over the development process.
The secure development lifecycle makes sure the software system abides by the relevant estimated requirements. However, it may not work perfectly in cases where there is some degree of uncertainty.
Have any doubts about how SDLC works?
We have a talented team of Professional experts in the field. Feel free to drop us a line to receive a relevant consultation.
How Does A Secure SDLC or Secure Development Lifecycle Work?
Every business wants to reduce the cost of product launch; with secure SDLC, companies and developers can reduce cost reduction and complete productions faster. It helps point out high costs, inefficiencies, risks and fixes them.
A secure SDLC is a less vulnerable SDLC process with more security infixed in all of the phases.
So how does a secure SDLC work?
Organizations with the SDLC process will need to add more security mechanisms in place. For instance, prioritization, remediation tools, and automated detection tools may need to be incorporated into the systems involved.
This helps resolve potential risks like bugs and other security threats in real-time. In effect, a secure SDLC involves lots of steps in the making of the software application.
Steps in secure SDLC are further divided into assignable tasks that need to be completed and then monitored and measured.
How Do You Achieve It?
To achieve a secure SDLC process entails paying a lot of attention to details. Implementing an elaborate and clear plan of action is a great way to avoid security issues.
The use of proper safety tools Information is a sure way to increase efficiency and continuous check for threats.
Information security is also a priority in creating a secure SDLC.
Besides, there’s the need to maintain a high product standard. This can be incorporated in the process by outlining the tasks that a particular software application may require to reduce waste and improve efficiency.
Also, by effective monitoring, the software project remains on course to become a viable investment for the organization involved. With lots of steps involved in the whole secure software development life cycle process, there can be a subdivision of stages.
How Many Steps Are There In A Secure Development Lifecycle Process?
Every single phase of the secure development lifecycle is expected to contribute to security. SDLC should be prioritized while maintaining solid and coherent communication with clients and end-users.
Developers and stakeholders interpret secure SDLC in many ways, but the process is related.
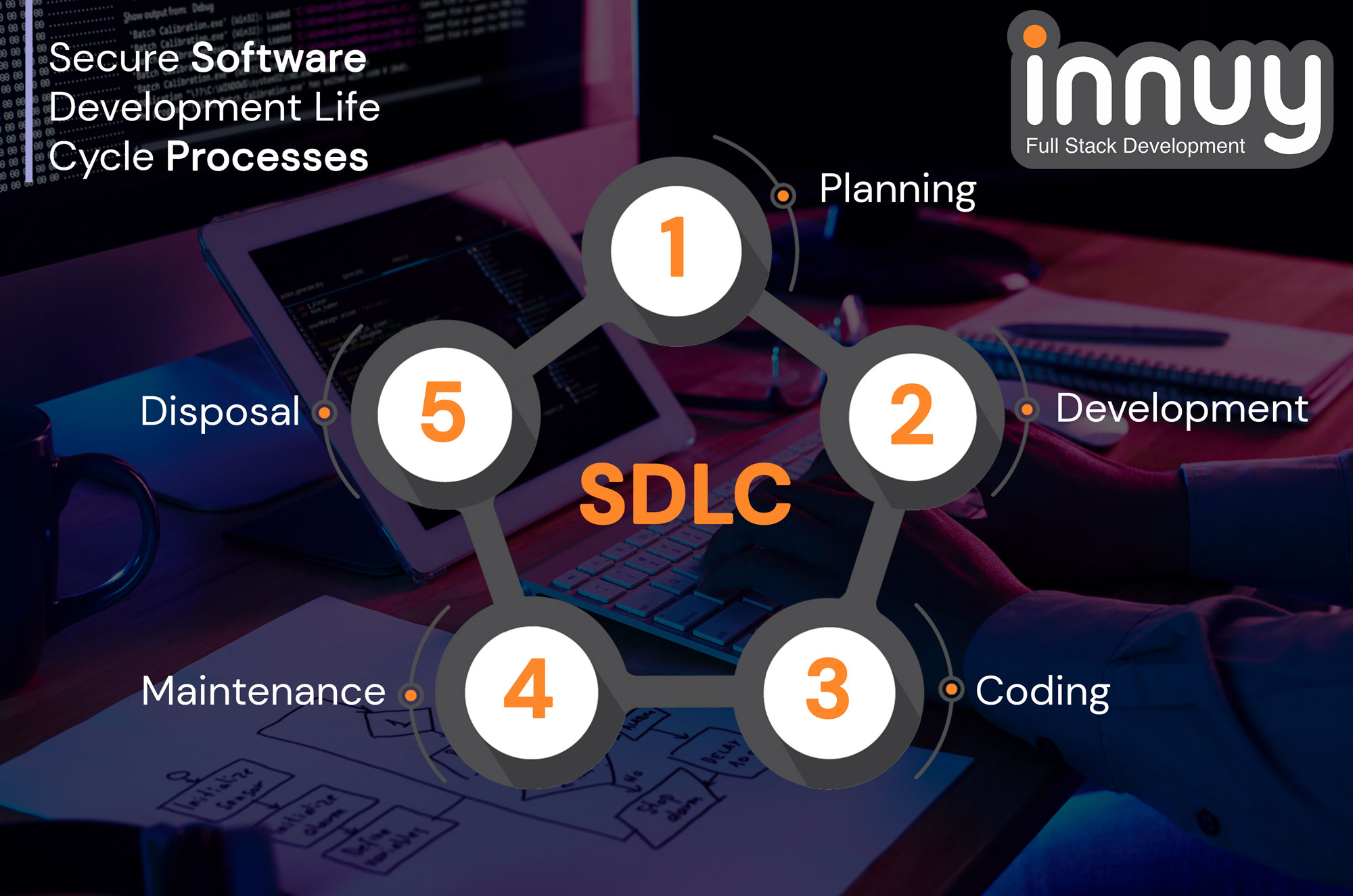
Here are some of the most commonly agreed-upon steps or phases in the secure development lifecycle process:
#1. Planning, Initiation/Requirements Analysis Phase
The requirement analysis, planning, or initiation phase is the first phase in the secure SDLC process. Some versions may have it as just planning, but the first involves way more than planning.
Proper adherence to this first stage of the secure SDLC process means more money, time, and resources are used. All of this combines for a smooth, safe process.
This first stage’s planning aspect involves allocating material and human resources to the relevant places they’re needed. Planning includes project scheduling, capacity planning, supply of provisions, cost estimation, and feasibility assessment.
The planning phase correctly identifies the system, makes project plans and process diagrams, and performs a detailed analysis.
During the planning stage, collected data and defined project goals are converted into more specific system functions for development.
In essence, this stage offers more coordination synchronization between development staff and project managers with security teams. This is done to ensure that a comprehensive, multi-perspective approach to the secure development lifecycle process is maintained.
Some security considerations should be adhered to in this first phase of a secure SDLC. Firstly, key areas that require security in the system should be found out on time.
Next, the information needed for security requirements needs to be evaluated. Also, every human resource working on the project should understand all of these considerations.
In summary, this stage identifies problems and goes further to create a plan to solve these problems or loopholes. Here are some elements of the planning, initiation/requirements analysis phase:
- Communication should be maintained with clients, consultants, employees, and suppliers. This is done to seek out possible different solutions to rising issues with the secure SDLC process.
- Definition of the project’s objectives and what the end-users expect or require.
- Identification of all the resources like finances and human resources that is available for use.
- The need to perform system studies and feasibility studies. Summarily, it should aim to create a product from the secure SDLC process better than those of competitors.
#2. Development Phase
After the first phase of planning and requirement analysis, the next phase is the development or acquisition stage. Developers begin the actual development of the product after they understand the requirements of the end-users.
This stage is usually considered as a part of the conceptual design. Here, the elements that the system requires are defined.
Also, a range of components like modules, architecture interfaces, and security levels will be deliberated. Besides, there’s the need to consider what type of data the system will support.
The evaluation and identification of the various design alternatives are also priorities in the development/acquisition phase. There’s a need to consider developing and delivering the secure SDLC design specifications too.
Different security considerations will make this phase solid and wholesome to the secure development lifecycle. There’s a need to conduct risk assessments and test for the security and functionality of the system.
Also, the team should prepare the initial documents needed for accreditation and certification of the system. Then designing the security architecture and developing security plans is also crucial to a secured SDLC.
#3. Implementation/Coding Phase
The next stage of the implementation or coding phase is where the software development’s actual physical design takes place. This phase is quite broad, and all designs from the development phase get converted to software.
From the implementation phase, we get an output of the development of codes and databases and infrastructure development for IT.
In developing, implementing, or coding the software, lots of expectations and suggestions from relevant parties are involved.
For this reason, all suggestions from the parties involved in decision-making, including from the business sphere, are considered. At the end of the phase, software that meets end-user requirements is available for testing and subsequent deployment.
Multiple security considerations are necessary for the implementation or coding phases of the secure SDLC process. There’s a need to avoid a conflict of the system elements with existing controls.
To achieve this, the designers have to ensure all of the system elements align with security specifications. All of the security features need to be enabled and configured correctly, and the system’s security functionality must be tested.
But in all, the relevant human resource should obtain the necessary formal authorization needed to implement the systems mentioned.
What is essential is to ensure that the whole system functions as a single entity. To achieve this will mean carrying lots of testing by trained personnel, automated systems, or even users.
All of these may take a significant amount of time to achieve. However, the endgame is the perfect customer satisfaction the system will bring.
In summary, this phase of the secure SDLC takes the end-users combined efforts and the designers to succeed. Elements like the writing of codes and the physical building of the system are carried out.
Here are some other elements of the implementation or coding stage:
- Design of the various items like input, output, programs, procedures, controls, and database.
- The installation of both software and relevant hardware.
- Depending on what the project is, another element involves converting between old and new systems.
- Running tests on the system.
- Giving adequate personnel training on how the system should be used
- Perfecting the different elements of the system to correct the issues that may linger.
#4. Operations Maintenance Phase
The next phase of the secure development lifecycle is the operations maintenance stage, and it is an equally crucial phase. As soon as the software is available to users, there’s a need to monitor it regularly.
This secure SDLC phase involves the periodic updating of the software, systems maintenance, changes, and adjustment. It also includes extending support to the system users for quality usability and the system’s sustained relevance.
Some security considerations are required to complete the operations maintenance phase of the secure development lifecycle.
For instance, there’s a need for consistency in monitoring the system to stray from the clients’ established security requirements.
Also, there may be a need for security system alterations in the secure SDLC process when they’re needed.
There’s also the need to configure the management activities to make sure the program stays consistent. Finally, changes in the system must be appropriately documented to analyze their possible effects.
Operations maintenance is an ongoing process in secure SDLC. It continues up until the discovery of a new issue in the system.
The eligibility of the software for periodic updates will depend on the policies of the company involved. Here are some requirements of this phase of the secure development lifecycle:
- There’s a need to analyze the feasibility of some elements like legal requirements, value, technical parts, economic value, operation and scheduling need, and their relevance to the system in the long term.
- Delivering improved systems when necessary
- Periodically replacing old hardware.
- Providing updates for specific components to ensure they meet standards
- Regularly evaluating system performance as the secure SDLC progresses
#5. Disposal Phase
The final phase of the secure development lifecycle is the disposal stage which some may not consider as crucial as the rest.
This phase is crucial because any error allowed could leave the company or organization at significant risk of divulging delicate information.
This phase has to do with the system’s disposal when it becomes irrelevant, redundant, or ineffectual.
For this stage, planning is done to dispose of the system information software and hardware. Also, arrangements need to be made to facilitate a transition of the secure SDLC to a new system.
One such arrangement is information movement to the new system if need be, or disposing or archiving it.
At the end of the secure SDLC’s disposal phase, the whole secure development lifecycle begins again. With time the systems involved develop to meet up with the improved technology or the change in needs.
Are you thinking about starting a New Project?
You can receive a relevant consultation from Secure Development Lifecycle Process experts. Simply click on the link below.
Best Practices For A Secure Software Development Cycle Process
In addition to following the phases of a secure SDLC, there is a need to keep some best practices for optimum results.
Problem-solving and working with many human resource personnel means that there are bound to be mistakes made. But the following best practices can be followed to make the process seamlessly successful.
#1. Specify Your Requirements
It is vital to have precise requirements so that there is no difficulty in understanding what is created. For this reason, developers and their teams should have specific requirements that are easily executable.
Vulnerabilities exposed during tests should be handled appropriately and immediately. The secure SDLC process should be a solution-oriented one as much as it is already one for problem finding.
#2. Developers Should Be Appropriately Educated
The secure SDLC process requires specific knowledge from the developers involved. Developers should be appropriately educated on aspects like the creation of a secure coding guideline.
Also, they should be provided with secure coding training and security awareness before the project begins. Besides, clear expectations regarding how fast issues or risks found out are handled should be set.
#3. Focus On Solving The Big Problems Before Others
The big problems are usually the more critical and demanding issues that need fixing. A good approach would be to focus on them instead of fixing all the project’s threats or loopholes.
This is especially helpful in applications or software that are bigger. Fixing newer and smaller issues in place of the big ones won’t be feasible in that instance.
Focusing on the problems in the secure development lifecycle helps stop problematic issues from entering production. With this approach, they are handled on time.
#4. Cultivate A Growth Mindset Among The Team
One way to go about the whole secure SDLC process and succeed is to keep an open mind. This approach should be cultivated amongst the security team working on the project as well.
It will help developers to further enhance the security of their applications.
What Follows An SDLC: BSIMM
The BSIMM or Building Security In Maturity Model measures software security. This framework is a data-driven mo
del that was developed from exhaustive software security initiative (SSI) analysis.
The BSIMM data-driven model has been built around a security framework for software-defined by 4 domains. Each of these 4 domains is further divided into three specific practices as well.
Here are the 4 broad domains that the model is built around:
- Deployment: Software Environment involves platform patching, operating system, change management, application monitoring; Configuration and Vulnerability Management; Penetration Testing.
- Governance: Training, Strategy and Metrics; Policy and Compliance.
- Touchpoints for Secure Software Development Life cycle (SSDL): Code Review; Security Testing; Architecture analysis.
- Intelligence: Requirements and Standards; Attack Models; Security Features and Design.
Some Popularly Used SDLC Models
The Software Development Life Cycle has some methodologies that are widely used. These are some of the popular models of the SDLC:
-
Agile Model
The Agile methodology promotes the continued interaction of testing and development in a project as the SDLC progresses.
In this method, the whole project is grouped into lower incremental builds provided in iterations. These iterations usually last between 1 to 3 weeks.
-
Incremental Model in SDLC
For the Incremental methodology, the requirements are grouped at the beginning of the project. The Software Development Life Cycle model is used for each group to develop the software.
So, the SDLC process is done until all of the requirements are completed. For this method of SDLC, the cycles serve as the maintenance phase of the previously released software.
The incremental model changes permit the development cycles to overlap after starting before the previous process is finished.
-
Spiral Model
The spiral model is yet another software development life cycle methodology. It is a risk-driven process model that aids the team in adopting elements of multiple process models like an incremental or waterfall.
It is a combination of concurrency and rapid prototyping in development and design activities.
-
V-Model in SDLC
In the V-model of the SDLC, phases are planned in a parallel manner. This means that the validation and verification phases of the software development life cycle are scheduled in parallel.
-
Waterfall model in SDLC
The waterfall model is one of the widely used and accepted software development life cycle models. All the process of software development for this method is grouped into the different phases of the SDLC.
Hence, the input of one phase is the outcome from the phase before it. The waterfall method is regarded as being documentation-intensive because earlier stages document the future actions followed by subsequent steps.
Want to start working with a team with vast experience in SDLC?
At Innuy, we are here to help you and answer your questions.
Conclusion
In recent times we’ve seen the increased demand for more robust cybersecurity measures. Alongside it is the need for more streamlined and sustainable development models to be created.
A key to this demand will be in understanding all of the secure SDLC process phases or steps. Secure development lifecycle or secure SDLC helps developers and organizations plan, create, and put out top-notch products.
This is in the sense that products in the secure development lifecycle process are delivered on time. Also, they are created in a programmatically competent manner.






Normally I don’t read post on blogs, but I wish to say that this write-up very forced me to try and do so!
Your writing taste has been surprised me. Thank you, quite great post.
Thanks very interesting blog!
Thank you for the good writeup. It actually was once
a amusement account it. Look advanced to far added agreeable
from you! By the way, how could we communicate?
Hi! Thanks for your comment. You can get in touch at hello@innuy.com